
Unless you consider ten (10) years in the hoosegow some odd form of payment, it’s widely known that (all together now) crime doesn’t pay. Martin Gottesfeld, 34-year-old Massachusetts knucklehead, just got reminded of it the hard way, though. He got sentenced to a decade behind bars for cyberattacking two (2)

Estimates vary (greatly), but industry analysts predict the SD-WAN market will clock in somewhere between $4.5 billion and $9 billion by 2022. Yes, that’s quite a variance, but whether it finishes at the high or low end, the growth is staggering considering it’s now just shy of $1 billion. Yeah,
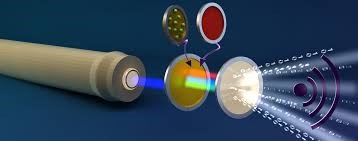
What do you use dozens, perhaps hundreds, of times a day without taking notice? Nope, it’s not your smart phone, TV or refrigerator…the light bulb. Yes, the light bulb, that ignored, often cursed (when the filament disintegrates at the most inopportune time) staple of every day life. Can we comprehend

It’s impossible to know what fish will bite on, which is probably why people are drawn to fishing. Sure, it seems a little odd that human beings take pleasure in outwitting something with a pea-sized, waterlogged brain, but, yes, it’s fun. One (1) day fish like cheese, the next day,





GDT Innovation Campus | 999 Metromedia Place Dallas, TX 75247 | 214.857.6100
Copyright © 2019-2024 General Datatech, LP. All rights reserved. GDT names and logos are trademarks, or trademarks Reg. U.S. Pat. & TM Office, of General Datatech, LP and/or its affiliates in the U.S. and other countries. Third-party trademarks mentioned or reflected herein are the property of their respective owners. Additionally, the use of the word “partner” does not imply a legal partnership relationship between GDT and any other company.
Copyright © 2019-2024 General Datatech, LP. All rights reserved. GDT names and logos are trademarks, or trademarks Reg. U.S. Pat. & TM Office, of General Datatech, LP and/or its affiliates in the U.S. and other countries. Third-party trademarks mentioned or reflected herein are the property of their respective owners. Additionally, the use of the word “partner” does not imply a legal partnership relationship between GDT and any other company.